Open-Source Software Security
Open-Source Code gives programmers the speed and agility to develop new capabilities, as well as to quickly achieve functionality which might take them weeks or months to develop. And open software gives developers greater flexibility at a significant savings as most open-source software is distributed freely. Most organizations estimate that open-source code makes up 60-80% of their proprietary application.
Open-Source Code is offered mainly by developers or group of programmers to be reused, copied, modified and utilized in developing web applications. This has made website development, gaming sites and custom applications faster and more economical than writing the programs from scratch. Web developers can take advantage of open-source packages, modifying and adding code to their requirements. Additionally, it can add dependencies that are incompatible with your existing software and could contain hidden malware.

Open-source frameworks and libraries can be effective for creating robust applications but there are vulnerabilities to be considered:
-
Security: Adopters of open-source technology may fall victim to code that does not follow best practices for application security. The Vulnerabilities include Malware Injection, Distributed Denial of Service (DDoS) and Data Exposure.
-
There are some other Coding Vulnerabilities like SQL Injections, Cross-Site Scripting (XSS), Insecure Direct Object Reference (IDOR), Cross-Site Request Forgery (CSRF) and Security Misconfiguration which developers are aware of but not all open-source projects have been addressed.
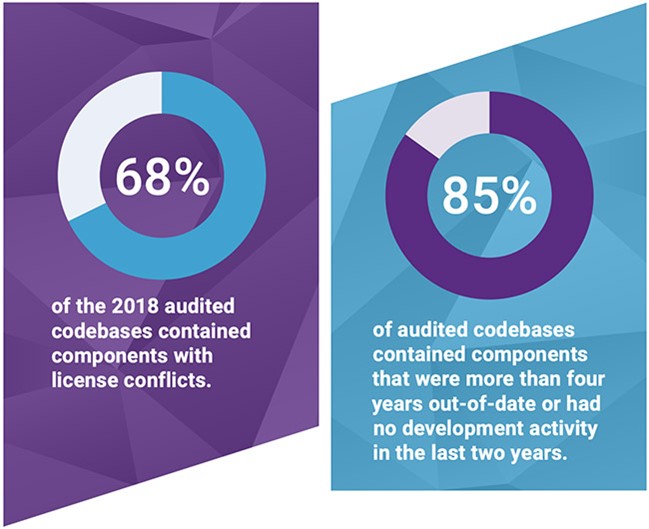
Open-Source software has many advantages but same way it has risks involved. It will be difficult for organizations to have enough visibility on their Open-Source software and a new research tells us that the security vulnerabilities which are in open-source software go undetected for more than three to four years before being disclosed. Because open-source software is community driven and there is no single or central authority responsible for quality and maintenance. Source-Code can be copied and cloned, leading to outsized complexity with versioning and dependencies. Worse is attackers can become maintainers and introduce malware.
Securing open source is an essential part of securing the supply chain for every company. Open-Source carries strict license requirements and obligations that are often overlooked by development teams. But failure to identify and comply these obligations can expose your organization to legal risk. Managing open source can threaten to slow down the development speeds and velocity.
The NVD is a good source for open-source vulnerability data. But with an average 27-day reporting delay, it should not be your only source of information. Public sources, such as the NVD, are a good first step for information on publicly disclosed vulnerabilities in open-source software. But we should remember that there can be lags in the reporting of any given NVD CVE entry. Timeliness has always been a factor affecting the ability of the NVD to publicize security vulnerability data.
By using open source, organizations and development teams are trusting the open-source community to update and maintain the components, release patches, and monitor for security issues. Although organizations acknowledge a heightened level of risk, unfortunately, most don’t effectively track or manage open source throughout their entire codebase and cannot easily address the widening hazards they face.
Biggest problem arises when Open-source community find out security vulnerability in Open source code. Open-source community releases new version with fix of vulnerability so users can correct this code. Most of the organization doesn’t know what all open-source component they have in their product source code so they never bother about these security fixes which gives chance to exploit this vulnerability to cause data leaks, financial fraud or other kinds of damages.
To conclude, it is very important to all the organization who are developing software for applications or devices to find out what all open-source components they have and if they are using latest update of Open source libraries to make sure their applications are secure and can’t be breached due to known open source vulnerabilities.


